When the shit hits the fan
 Today I was asked to bring back a website to life that was brought down by what turned out to be a Brute Force attack, also known as DDOS (Distributed Denial of Service) attack. The load on that site was so high that the hosting provider shut the site down to prevent other sites from experiencing performance problems (it was hosted in a shared environment). The hosting provider told them to first fix the problem before they could restore the site...
Today I was asked to bring back a website to life that was brought down by what turned out to be a Brute Force attack, also known as DDOS (Distributed Denial of Service) attack. The load on that site was so high that the hosting provider shut the site down to prevent other sites from experiencing performance problems (it was hosted in a shared environment). The hosting provider told them to first fix the problem before they could restore the site...
Nowadays it is relatively easy and cheap to bring down a website via a Brute Force Attack.
I see attempts to hack my site multiple times a week. So the question is not: ‘When will it happen to you?’ because it may already be happening right at this moment.
How does a Brute Force Attack work?
The hacker has control over an ‘army’ of mall-ware infected PC’s. The hacker can 'instruct' those PC's to visit e.g. your website's login url’s. Once found they will try to login to your site by trying to guess the user name and password. All this is automated for the hacker!
I have seen attacks on my website with thousands of simultaneous connections, each connection being served a web page by the CMS (= server load).
If the attack lasts long enough, your website will be slowing down by the minute until it will eventually run out of CPU and / or execution time with your hosting provider and everything grinds to a hard stop.
I have drafted up some tips for you that you can already implement today: because it is better to be safe then sorry.
Tip 1: Host with a responsive and knowledgeable Hosting provider
The question is not if your site is going down, but when your site is going down. When that happens you will learn to appreciate your hosting provider who can instantly give you access to your site (back-end) and has the knowledge to help you and take appropriate first steps.
I have seen my share of (cheap) hosting providers that are only available via a support ticket and let you wait for hours before they respond and when they respond they tell you to hire a professional because they have no expert knowledge of your used CMS: "first fix the problem, then we will bring your site on-line again..."
I host my own websites with SiteGround: top and responsive 24/7 support and expert knowledge of both Joomla! and WordPress.
Tip 2: Password protect your website administrator directory (admin area)
I know: there are plugins that ‘hide’ your login page behind a token or different url, but that only solves part of the problem. Your CMS is still put to work to serve the attacker just to find out that they do not have the correct token or url. So although you make it harder for the hacker to try to login, the load on your server is still partially there.
By blocking your administrator directory with a .htaccess / passwd rule, the hacker is stopped before your CMS is putting load on your servers cpu.
In your hosting provider's cPanel, just click the 'Password Protect Directories' button and follow the on-screen instructions:
This will work for your back-end login page, but it doesn’t work for your front-end (user) login page.
Tip 3: Block all IP addresses after 3 failed login attempts
Now this is where I advice you to install a plugin (I use Brute Force Stop (Joomla!) for that). This plugin will monitor your login service. When a visitor fails to login after three consecutive times (configured) its IP address is automatically added to your website's .htaccess file.
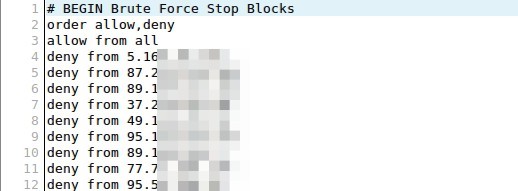
Again: blacklisting the IP addresses via a plugin in your CMS works to prevent the hacker from login in, but it will not decrease load on your website's server. It is best if you deny access via .htaccess as this will directly drop the load on your server.
Why three times and not 4 or more times?
Experience learns that the hacker will only try three times per IP address before he / she moves on to try with the next IP address. When he used his last IP address he will start from the first again which will now fail because it is blocked by your .htaccess file.
Tip 4: Change the name of your administrator user to something else then admin
When I look in my log files at what login names are tried by the hackers, number 1 being used is ‘admin’.
Runner up is my domain name (so for my site I see a lot of ‘onlinecommunityhub’ in my logfile).
So make sure to change the default administrators login name from admin to something else!
Tip 5: Always use the latest versions of your CMS and components / extensions
This goes without saying: Better to be safe than sorry :)
Pro tip: Test restoring your backups
Remember that you periodically need to check your backup via a restore: I have seen my share of successful backups that where useless because they could not be restored! Make sure you test your restore!
I really hope that you will never experience a hacked site or a website that is unavailable because of a Brute Force attack. Implementing these tips will for sure make your website more resilient to these hacks.
Do you have a tip? Please add it as a comment below this article and help others benefit from your experience!