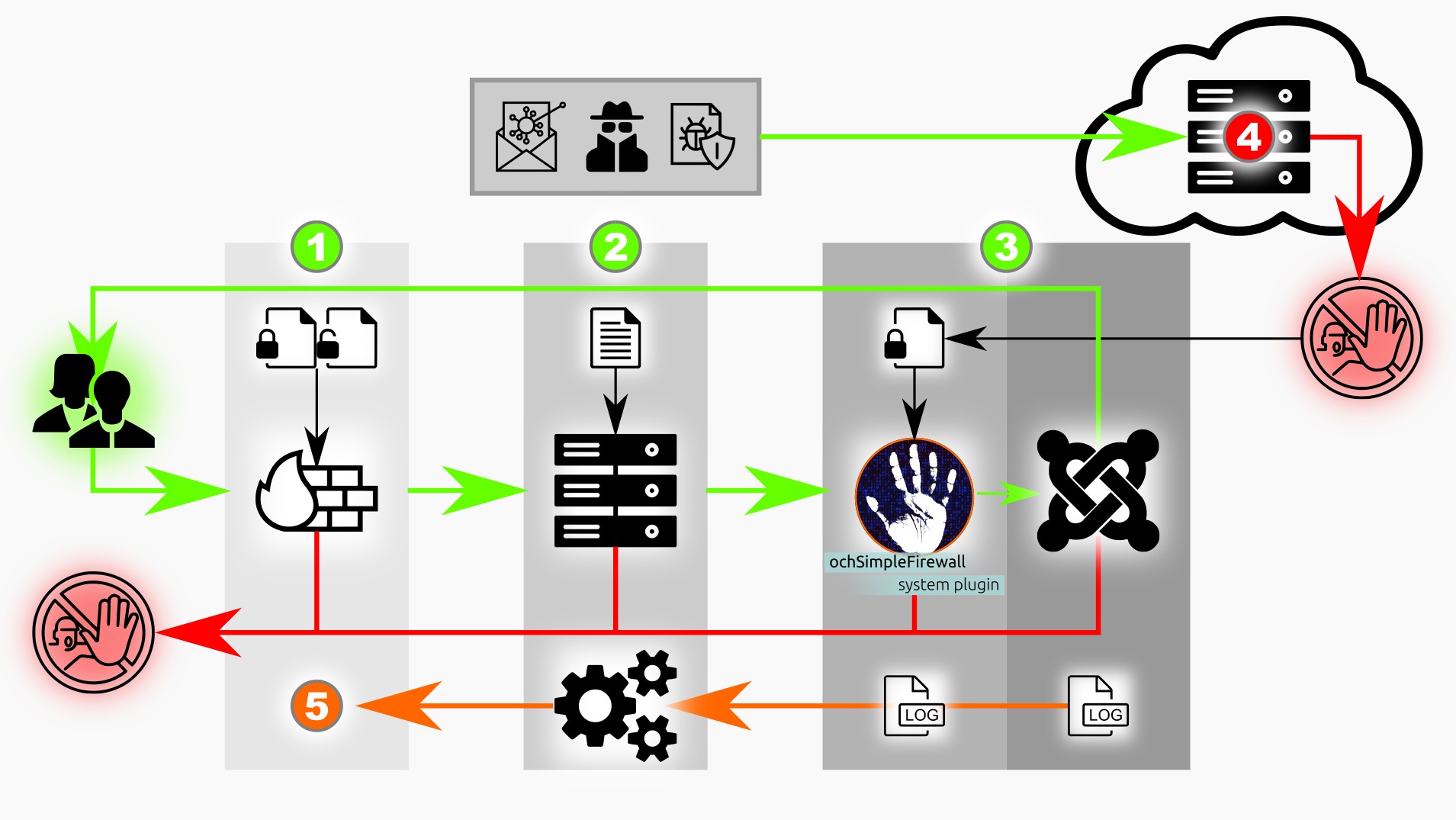
This blog will give you a high level schematic overview of how you (and your hosting provider) can add effective and efficient ways to stop abusers, hackers, spammers and other ‘digital-low-life’ from messing with your site (further referred to in this blog as: abuser(s)), your site resources and your site visitors / customers.
The Image in this blog is used as the schematic, starting from the left, with visitors visiting your site and the security ‘zones’ they need to pass to actually see the web page in their browser.
Rule of thumb when securing your website is that the best place to stop an abuser is as early as possible in the flow. So stopping an abuser should be done in Zone 1, if that is not possible in zone 2 and if that is not possible in zone 3.
Important note: If and how the zones are secured / configured for your specific website depends on your hosting provider and if you are maintaining a VPS yourself; on your VPS server setup.
When your site is on a (shared) hosting platform you most likely have no control on zone 1 and only partially on zone 2 (Apache web server, .htaccess file).
Everybody has control over zone 3 as the tools here are installed in your website / Joomla! CMS.
Zone 1: The Firewall
As said, the best place to stop an abuser is in the firewall zone: the firewall is either a hardware firewall or a so called server side firewall. The firewall filters incoming (and outgoing) traffic based on configured tables. In the table there can for example be a rule to block all traffic for a specific IP port. Or block traffic originating from an IP address or a Range of IP addresses.
Firewalls are in principle very basic in their operation: no matter what data you post or what URL you visit, you are blocked or allowed based on the visitors ‘envelope’ information (from – to IP information).
Zone 2: Web Application Firewall / Web server .htaccess
A Web Application Firewall (WAF) inspects what is in the envelope. It has a set of (maintained) rules that validate and check the contents of the visitors requests and the server’s responses. A popular WAF is ModSecurity. ModSecurity is an Open Source Web Application Firewall originally build as a module for Apache HTTP Servers (but nowadays also available for Nginx, IIS, etc.). It can be configured to download and use rules from a managed rule repository: so when a new thread / attack is identified and added to the maintained rule set, your site is then automatically protected against that specific attack on your website.
Another (important!) protection mechanism in zone 2 is the .htaccess file for your Apache web server.
With .htaccess files you can block visitors (identified by their IP address), or password protect files or directories on a web server level. Regardless of what hosting plan you are on, you will always have access to your sites .htaccess file and can (and should!) use that to secure your website.
Zone 3: Joomla CMS with extensions / plugins
This is your last line of ‘defense’. This is where user authentication comes in and for unregistered visitors tools like a captcha. The best possible ‘Protection’ however on this level is moderation, although this unfortunately is most likely only done after abuse via or of your site.
If you run a forum on your site (like e.g. Kunena), you will see that abusers first manually register on your website, next they will create some legitimate forum posts or topics to build credibility, ‘fooling’ your spam algorithms / tools. Finally they will start to use bots that will login as that user and start posting spam. Spam that is then automatically delivered via mail to everybody who is subscribed to that topic.
So you ‘catch’ the spammer, remove the messages (apologize to your users?), remove the user account and if done correctly block the spammer's IP address from accessing your website. Either with a tool or via adding it to the block section in the .htaccess file. So you just learned the hard way that visitor with IP address a.b.c.d is an abuser.
Zone 4: The vast Internet (Security) Community sharing abuser information
How effective would it be to able to block a visitor based on him being ‘caught’ abusing other websites?
This is where ochSimpleFirewall comes into play to effectively and efficiently prevent known abusers from messing with your site and your visitors / customers.
I have managed in a security project for a large (global) enterprise in the Netherlands (banking sector). The project’s deliverable was a SIEM (Security Information and Event Management) department. The designed SIEM utilized several lines of defense ranging from highly specialized multi-level firewalls, hardware (and software) Intrusion Detection and Prevention Systems (IDS/IPS) and (external) DDOS mitigation solutions. Information of ‘caught’ attackers was in real-time shared with and analyzed by security companies. These security companies maintain a knowledgebase of these abusers categorized on type of abuse and use that information to make their services better and protect the internet.
In a constant ‘battle’ against these abusers, the majority of these security companies share these knowledgebases in the form of ‘netsets’. A netset is a list of IP ranges and / or IP addresses.
OchSimpleFirewall lets you download (and cache) these (often hourly updated) maintained netsets and will block a visitor directly when he has a matching IP address.
OchSimpleFirewall utilizes (a subset of) FireHOL IP Lists. FireHOL analyses all available security IP Feeds, mainly related to on-line attacks, on-line service abuse, malwares, botnets, command and control servers and other Cybercrime activities.
This enables you to stop abusers before they are able to abuse your site!
There are a lot of active forums on the internet, all targeted by spammers and bots. Most forum software has some kind of spam reporting tool integrated: when spam is posted, the moderator can label the post as spam and the spammers IP address is uploaded to a central repository. A good and widely accepted example of this is the Stop Forum Spam initiative.
Another tool is to analyze the post content with an algorithm offered by cloud services. When the post is identified as spam by these specialized services, the spammers IP address is retained by these services to better block spam on other sites. A good example of this kind of spam detection is CleanTalk. CleanTalk is a widely used cloud spam protection for forums, boards, blogs and sites: no Captcha, no questions, no counting animals, no puzzles, no math. Fight spam!
When you enable the StopForumSpam and / or CleanTalk netset in ochSimpleFirewall you are tapping in on the knowledge build up by hundreds of thousands of websites: blocking the abusers and bots before they can do any harm. No expensive API calls to external resources needed to validate an IP address!
But you said it is better to block in zone 1 (Firewall) then in zone 3?
True and if you are on a VPS, or on a hosting provider who utilizes and lets you configure a service called Fail2Ban, you can. More on that in a separate blog post!